Maintaining compliance with the evolving Cybersecurity Maturity Model Certification (CMMC) requirements is crucial for defense contractors and organizations. In this article, we’ll explore the recent revisions of the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 and their direct impact on CMMC compliance. As a leading provider of cybersecurity solutions, Back To Business I.T. aims to empower defense contractors with the necessary insights to navigate these changes effectively.
Understanding NIST SP 800-171 serves as the baseline for protecting Controlled Unclassified Information (CUI) on nonfederal systems and organizations. These guidelines establish essential security requirements that federal agencies and government contractors must follow when handling sensitive information. CUI encompasses data such as intellectual property, health information, and critical energy infrastructure information. Compliance with NIST SP 800-171 is a prerequisite for defense contractors seeking to secure Department of Defense (DoD) contracts.
The Impact of NIST SP 800-171 Revisions on CMMC Compliance
The revisions in NIST SP 800-171, particularly the upcoming Revision 3, significantly influence the compliance landscape for defense contractors pursuing CMMC certification. Let’s explore how these revisions affect CMMC compliance:
- Enhancing Alignment: NIST has aligned the language of SP 800-171 Revision 3 with the closely related SP 800-53 Rev. 5, enabling defense contractors to apply the technical tools and controls outlined in SP 800-53 to achieve CMMC compliance. This alignment streamlines the implementation process and ensures a consistent approach to cybersecurity.
- Strengthening Security Requirements: The revised NIST SP 800-171 places increased emphasis on cybersecurity, reflecting the evolving threat landscape and state-level espionage targeting CUI. The new requirements address specific threats to CUI and incorporate state-of-the-practice cybersecurity controls. By adhering to these enhanced security requirements, defense contractors can bolster their cybersecurity posture and better protect sensitive information.
- Simplifying Implementation: NIST SP 800-171 Revision 3 introduces clearer instructions and specific criteria, reducing ambiguity and facilitating easier implementation. This streamlining of requirements simplifies the compliance process and enables defense contractors to align their cybersecurity practices with the latest industry standards.
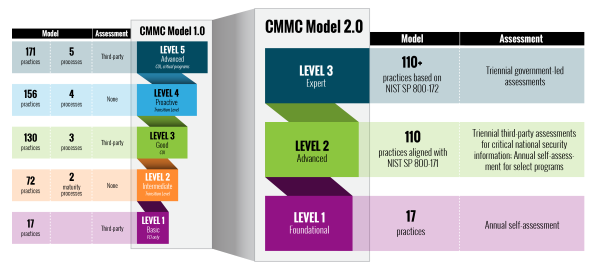
- Aligning with Future CMMC Levels: The revisions in NIST SP 800-171 provide a foundation for future CMMC levels beyond Level 3. By incorporating the enhanced security requirements and alignment with SP 800-53 Rev. 5, defense contractors get a head start in preparing for future CMMC levels, ensuring a smooth transition as the certification evolves.
To achieve CMMC compliance, defense contractors must remain up-to-date with the revisions in NIST SP 800-171.
The upcoming Revision 3 brings enhanced alignment, strengthened security requirements, simplified implementation, and a forward-looking approach to future CMMC levels. By effectively understanding and implementing these revisions, defense contractors can ensure their cybersecurity practices meet the rigorous standards required for DoD contracts.
Back To Business I.T. is committed to supporting defense contractors on their journey towards CMMC compliance, and we’re ready to provide tailored cybersecurity solutions. Take the first step today by scheduling a gap analysis with our expert cybersecurity consultants.