WHAT YOU NEED TO KNOW
The Cybersecurity Maturity Model Certification (CMMC) program establishes a set of standards that organizations must meet to be eligible to bid on or renew contracts with the U.S. Department of Defense (DoD). It is designed to protect controlled unclassified information (CUI) shared by the Department with its contractors and subcontractors. The program incorporates a set of cybersecurity requirements into acquisition programs and provides the Department increased assurance that contractors and subcontractors are meeting these requirements.
The framework has three key features:
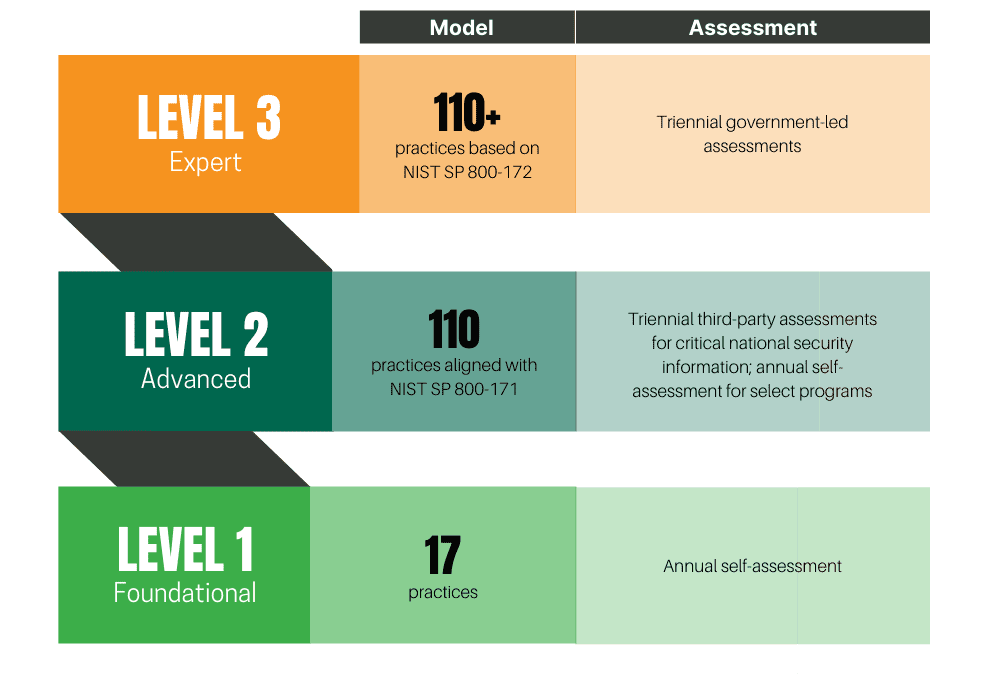
- Tiered Model: Companies entrusted with national security information are required to implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also sets forward the process for information flow down to subcontractors.
- Assessment Requirement: Assessments allow the Department to verify the implementation of clear cybersecurity standards.
- Implementation Through Contracts: Certain DoD contractors that handle controlled unclassified DoD information will be required to achieve a particular maturity level as a condition of contract award.
CMMC 2.0
In September 2020, the DoD published an interim rule to the DFARS in the Federal Register (DFARS Case 2019-D041), which implemented the DoD’s initial vision for the CMMC program and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
In March 2021, the Department initiated an internal review of CMMC’s implementation, informed by more than 850 public comments in response to the interim DFARS rule. This comprehensive, programmatic assessment engaged cybersecurity and acquisition leaders within DoD to refine policy and program implementation.
In November 2021, the Department announced “CMMC 2.0,” an updated program structure and requirements designed to achieve the primary goals of the internal review:
- Safeguard sensitive information to enable and protect the warfighter.
- Dynamically enhance DIB cybersecurity to meet evolving threats.
- Ensure accountability while minimizing barriers to compliance with DoD requirements.
- Contribute towards instilling a collaborative culture of cybersecurity and cyber resilience.
- Maintain public trust through high professional and ethical standards.
The CMMC program requires compliance for all prime and subcontractors currently doing business or who want to do business with the DoD (~300,000). More than 80,000 of these contractors will also require a CMMC compliance assessment and certification as part of their maturity level and handling of SUI.
BUSINESSES THAT MUST BE COMPLIANT:
➡ IT Services Providers
➡ Accountants
➡ Consultants
➡ Manufacturers
➡ Manufacturing Supply Chains
➡ Landscaping Services
➡ Janitorial Services
➡ And More…
If you’re a defense prime or subcontractor still in the beginning stages of CMMC compliance, the time to act is now. Preparation and implementation of the following requirements can take upwards of 18 months.
TO GET STARTED, CONTRACTORS SHOULD IMMEDIATELY:
➡ Identify their desired maturity level to bid on DoD contracts (below).
➡ Work toward meeting all 110 controls in NIST SP 800-171.
➡ Identify their current Supplier Performance Risk System (SPRS) score.
➡ Create a system security plan (SSP).
➡ Document plans of action and milestones (POA&M) to demonstrate how you intend to close any gaps for NIST SP 800-171 controls not yet met.
If you are unsure of your required maturity level to bid on contracts, we will help you identify it. Together, we will check your current network against NIST SP 800-171 and identify areas that need attention. Our consultants will then help create your System Security Plan (SSP) and Plan-of-Action & Milestones (POA&M) to provide as documented evidence for auditors.
CMMC MATURITY LEVELS AND FOCUS
UPDATES
Top 10 Cybersecurity Trends for 2024

Don’t be a Statistic: Protect Your Manufacturing Business Against Cyberattacks by Establishing a Policy of Cyber Resilience

The Impact of NIST SP 800-171 Revisions on CMMC Compliance
HOW WE CAN HELP
Our cybersecurity experts can perform a comprehensive gap analysis and determine your current SPRS score, as well as work with you on a plan to resolve any areas of non-compliance. As a full-service IT firm and the leading CMMC-AB Registered Provider Organization (RPO) in the area, we can also implement solutions to address gaps so you are both compliant and ready for CMMC certification.
1Assess
We conduct a thorough gap analysis and compare your current network with NIST SP 800-171 and CMMC requirements. This reveals areas to address for compliance.
2Plan
We prepare a System Security Plan (SSP) and Plan-of-Action & Milestones (POA&M) for you based on the gap analysis. This serves as documented evidence to show you're working toward compliance.
3Implement
We help you implement POA&M action items. The solutions can vary -- from something as simple as implementing multi-factor authentication to updating your IT infrastructure.
